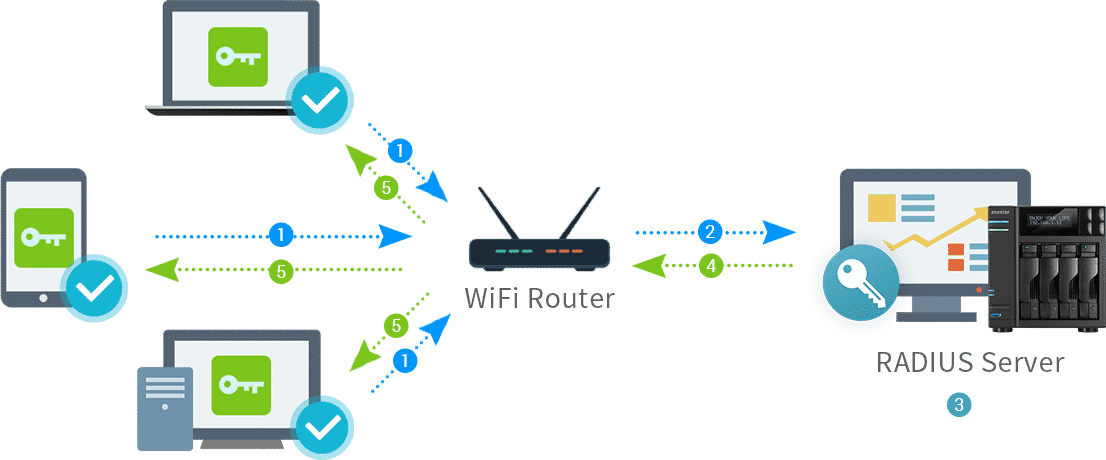
RADIUS stands for Remote Authentication Dial-In User Server. It is a protocol used for authorization and authentication. If you have a RADIUS server, you will have full control over who can connect your network and whom not to grant the access. This is applicable for all network types starting from wireless, VPN to direct and dial-up. Therefore, it is the middle layer in between the communication of the clients and servers.
All You Need To Know About RADIUS Server –
Along with that, the RADIUS protocol is applicable to proxy configuration whereby the proxy receives the requests and for authentication, it is connected to the server where the RADIUS role. RADIUS server helps a company to maintain profiles of the users in a central database which can be accessed by all the servers. This helps in better security management and setting up policy for server administration. It also helps in better tracking of network statistics and billing. In fact, it has become an industry standard and so many different companies are adapting to network products.
Working –
The process begins with a user sending a request to the server for accessing. The server receives the request and authentication begins. The client could send request from browser-based HTTPS connect or from mobile VPN. In the former case, the connection takes place through port the latter takes place through IPSec. The server takes in the username and password from the user and creates an access-request message and sends it to the RADIUS server. The password is encrypted in the access-request and there is also RADIUS access secret code so that it is not misplaced in the transfer process.
The RADIUS server receives the request and checks whether it has come from a known client server or not. If it is not, the request is rejected immediately and if it is found to be suspicious, the server can be blocked from further request. If the client server is a known one, then RADIUS server checks the shared secret code. The server also looks at the authentication method request. The authentication method must be within the allowed method.
If the authentication method is within allowed, then the user name and the password are accessed. The decryption is done and the credentials are matched with that of the database. Once matched, various user information and data are fetched to match with the access policy set in the server. All everything is compatible and matches, the RADIUS server sends a response. If the credentials or the policy do not match, the access is denied.
Conclusion –
The main competitor of the RADIUS server is LDAP server. So far, it is the market share, the LDAP server is the final authority and it has one protocol for authorization and authentication. On the other hand, RADIUS deals with authorization and authentication separately. Authentication is what the credentials are and authorization is about the policy. Therefore, we can say that it is indirectly the two-factor authentication which is very popular in today’s world.